Magecart is just one of 38 JavaScript-sniffing groups that have been stealing credit cards, account numbers, and other types of personal data from millions of online shoppers in the last year.
In 2018, they made headlines by hacking major sites like Ticketmaster, British Airways, and Newegg and was considered one of WIRED's Most Dangerous People on the Internet in 2018. In November 2019, Macy's announced they were compromised by Magecart. Now in 2020, it was revealed that Focus Camera was hacked in late 2019.
The Attack
Magecart injects their code onto websites by hacking first- or third-party JavaScript, like an advertising tag or a Magento plugin. Then they use that code to collect personal data and send that data back to their domain.
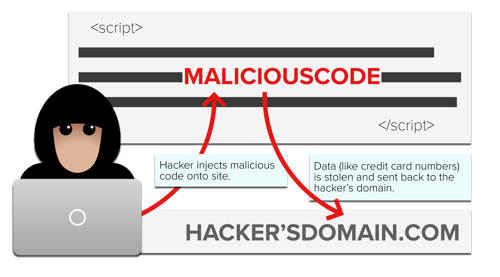
Since the malicious code is customized to work with the victim's site and is often only a few lines, it can go undetected for weeks or even months.
In Newegg's case, Magecart injected just 8 lines of code in their checkout process and stealthily created a domain called neweggstats.com to collect credit card information. The attack lasted 33 days before the code was identified by Volexity and quickly removed.
Here are the 8 lines of credit-card stealing code:
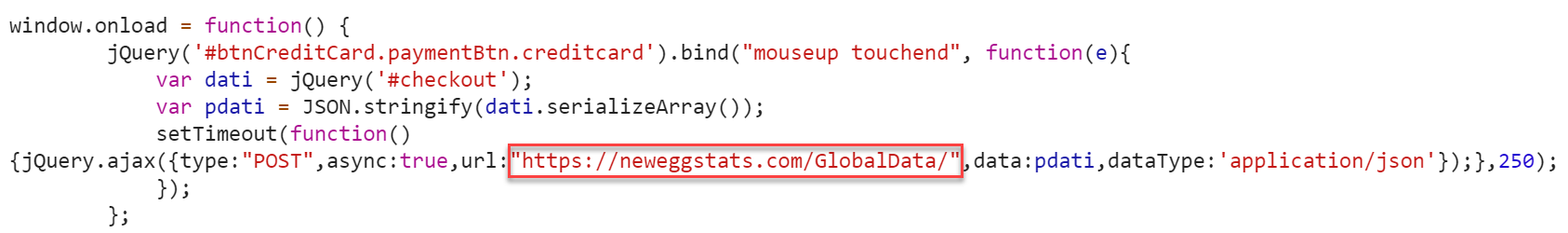
Source: Volexity
Magecart compromised Macys.com on October 7, 2019 in similar fashion. They altered a script on the Checkout and My Wallet pages and sent that data to barn-x.com. Macy's uses bam-x.com (owned by Narrativ) for personalization, so barn-x.com stayed well-hidden.
We're measuring Macys.com for our Retail Benchmarks and can quickly see when barn-x.com appeared.
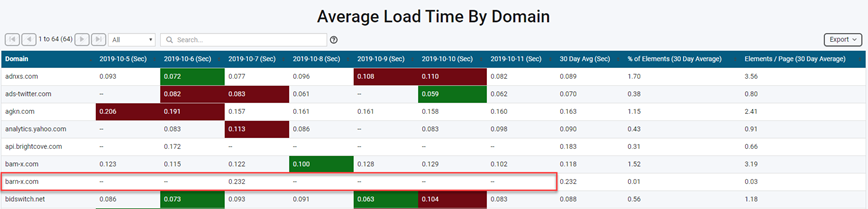
Source: Blue Triangle Tag Governance
Symptoms
Due to the sneaky nature of Magecart, there are very few ways for websites to diagnose whether or not they've been hacked.
- Banks and payment processors correlate a high volume of fraudulent activity to a common website and then notify the website. (most common)
- Customers file complaints of fraudulent activity with a website following a transaction.
- Security vendors like Volexity, RiskIQ and Trend Micro identify websites with compromised code.
- Scheduled website scans identify changes in JavaScript code composition. Then that code is scrutinized. (least common)
Treatment
Aside from identifying and removing the malicious Magecart code, US companies are required by law to disclose security breaches that impact customer data. As you can imagine, this impacts brand reputation and future revenue.
Ticketmaster UK was hit with a $6.5 million dollar lawsuit after they were hacked, and British Airways is facing a record-breaking GDPR fine of $229 million due to a Magecart attack that stole 380,000 credit card numbers.
Check out some of the headlines:
 Source: Google News
Source: Google News
But the treatment doesn't stop there. According to Dutch security researcher Willem de Groot, 1 out of 5 breached sites is "infected (and cleaned) multiple times". Websites must remain vigilant and take preventative measures to ensure they are not hacked again.
Prevention
To best prevent a Magecart attack, you need to:
- Secure your first-party code
- Mitigate third-party risk
- Block unauthorized transmission of personal data
Secure your first-party code
Ensure your web server infrastructure is up-to-date and fine-tune your web application firewall (WAF) to help prevent your first-party code from getting compromised.
Configure your WAF to block and alert you when there are potential code injection attacks (e.g. PHP Object Injection and SQL Injection). Set rules that block known Magecart domains from accessing your site.
It is important to note that these traditional security measures are not 100% effective because Magecart is compromising first- and third-party code as well as constantly registering new domains.
Mitigate third-party risk
Ticketmaster UK was hacked in June 2018 after Magecart injected credit card skimming code inside their third party chatbot vendor, Inbenta. In December 2018, Magecart compromised a retargeting script from Adverline, a French advertising firm. The Adverline hack impacted 277 eCommerce websites.
Magecart has moved from just hacking individual sites and their code to compromising third-party vendor code. This shift comes at a time when companies are adding more and more third parties to their websites for services like advertising, analytics, and A/B testing.
Across our retail customer base, third party content is on average responsible for 35% of a web page's weight and 61% of the number of files loaded.
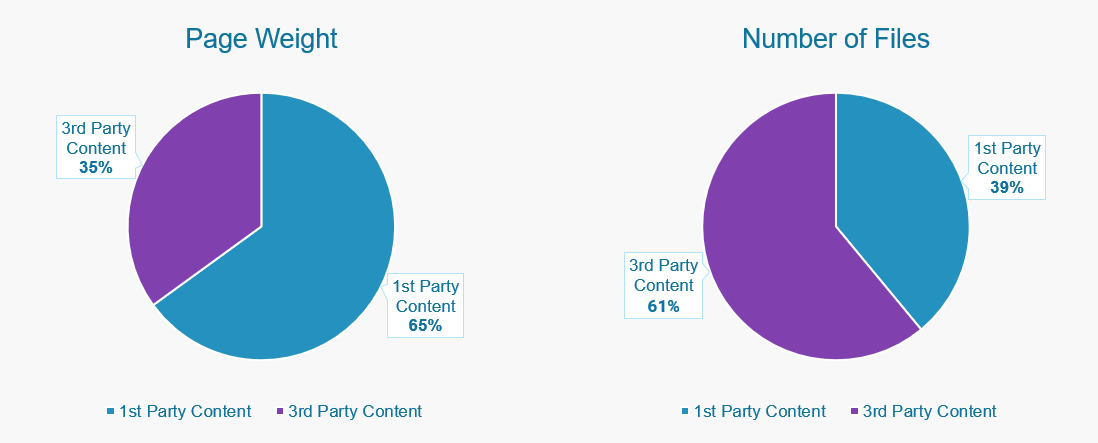
Source: Blue Triangle - Website Composition
Here are a couple tips to mitigate third-party vendor risks:
Scrutinize every third party loading on your website
First identify the third parties loading on your site, specifically the ones that have access to the most sensitive parts of your website (e.g. shopping cart, account signup, checkout).
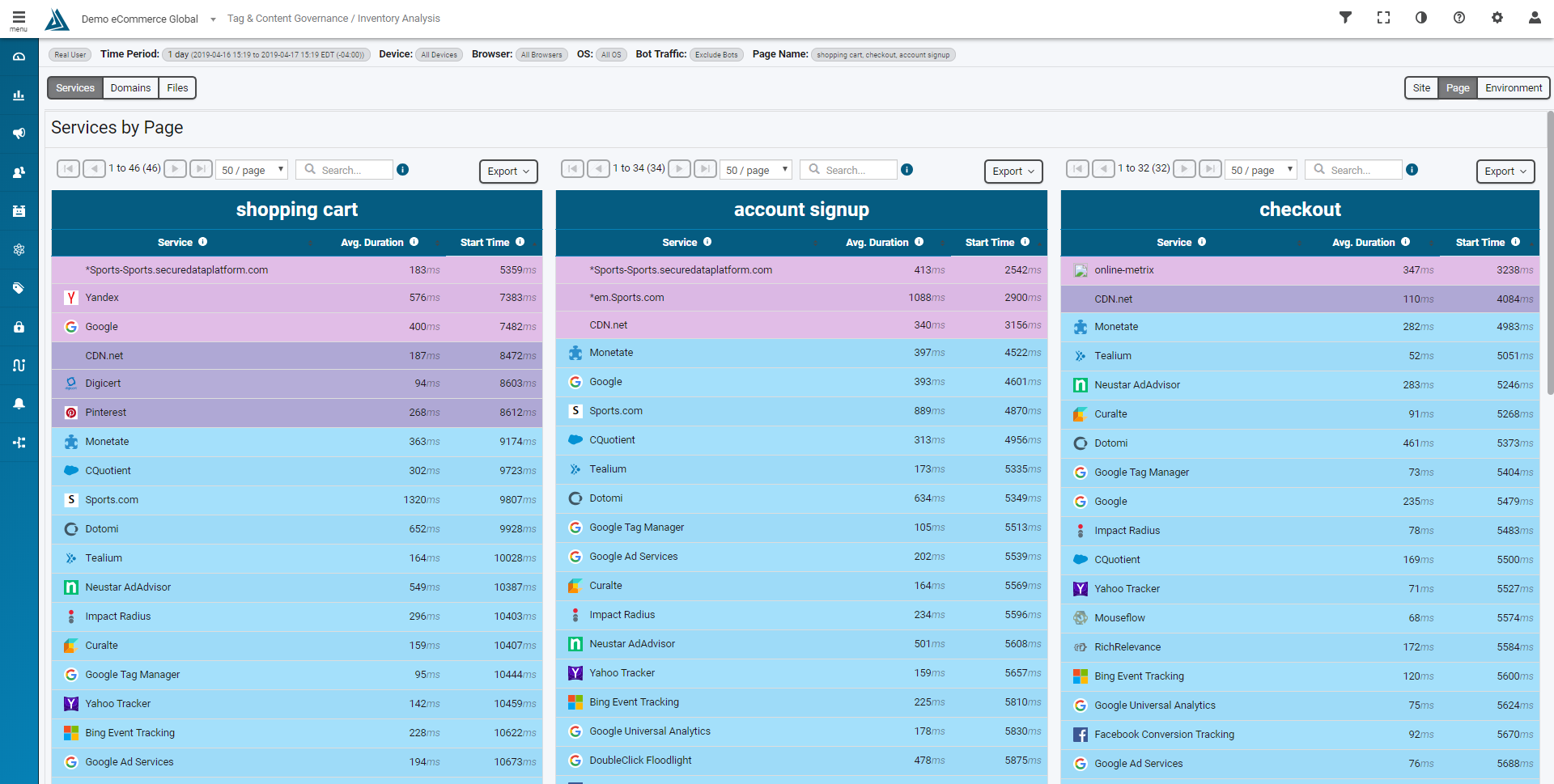
Source: Blue Triangle - Third Party Inventory by Page
Now for every third party on your website, ask yourself:
- Am I still using this?
- Is there another third party on my website that offers the same capabilities?
- Does it need to load throughout the checkout process?
- Is it loading other third party technologies (piggybacks)?
- Who in my organization owns this relationship?
From here you can make data-driven decisions on what third parties to keep and ensure they are loading exactly where and what they should be. The more control you have over your third parties, the more secure you will be.
Regularly conduct vendor due diligence reviews
Just one audit isn't enough; you need to regularly vet your third party vendors and their code.
In late 2018, thousands of eCommerce websites using Magento were breached after Magecart hacked 20 unpatched and vulnerable Magento extensions. This highlights the importance of ensuring your third parties are protecting their code and adhering to the latest security best practices.
Block unauthorized transmission of personal data
If your first or third party code is compromised, you need to prevent this code from sending personal data to a Magecart domain. The most effective way to stop this from happening is by implementing a Content Security Policy (CSP) - the last line of defense from Magecart.
A Content Security Policy (CSP) allows you to control what domains can access your website and what file types they are allowed to load. So if Newegg had a well-built CSP in place throughout their checkout process, the Magecart domain neweggstats.com would have been blocked from receiving credit card information.
Here's the graphic from earlier, but with a CSP in place.
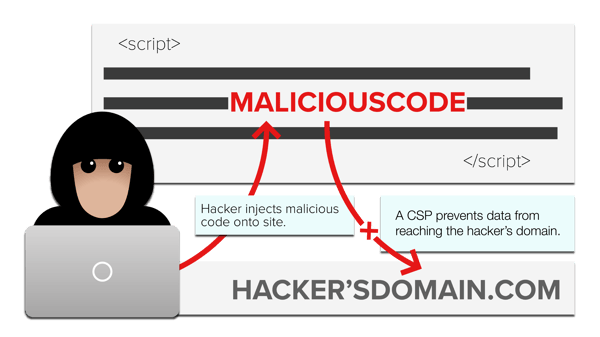
To properly build, implement, and manage a CSP, you need to:
- Inventory all the domains that have access to your site
- Determine what domains are "approved" and what resources they're allowed to load
- Build the CSP based on the "approved" domains
- Implement the CSP and update it with every site release
- Be alerted on CSP violations
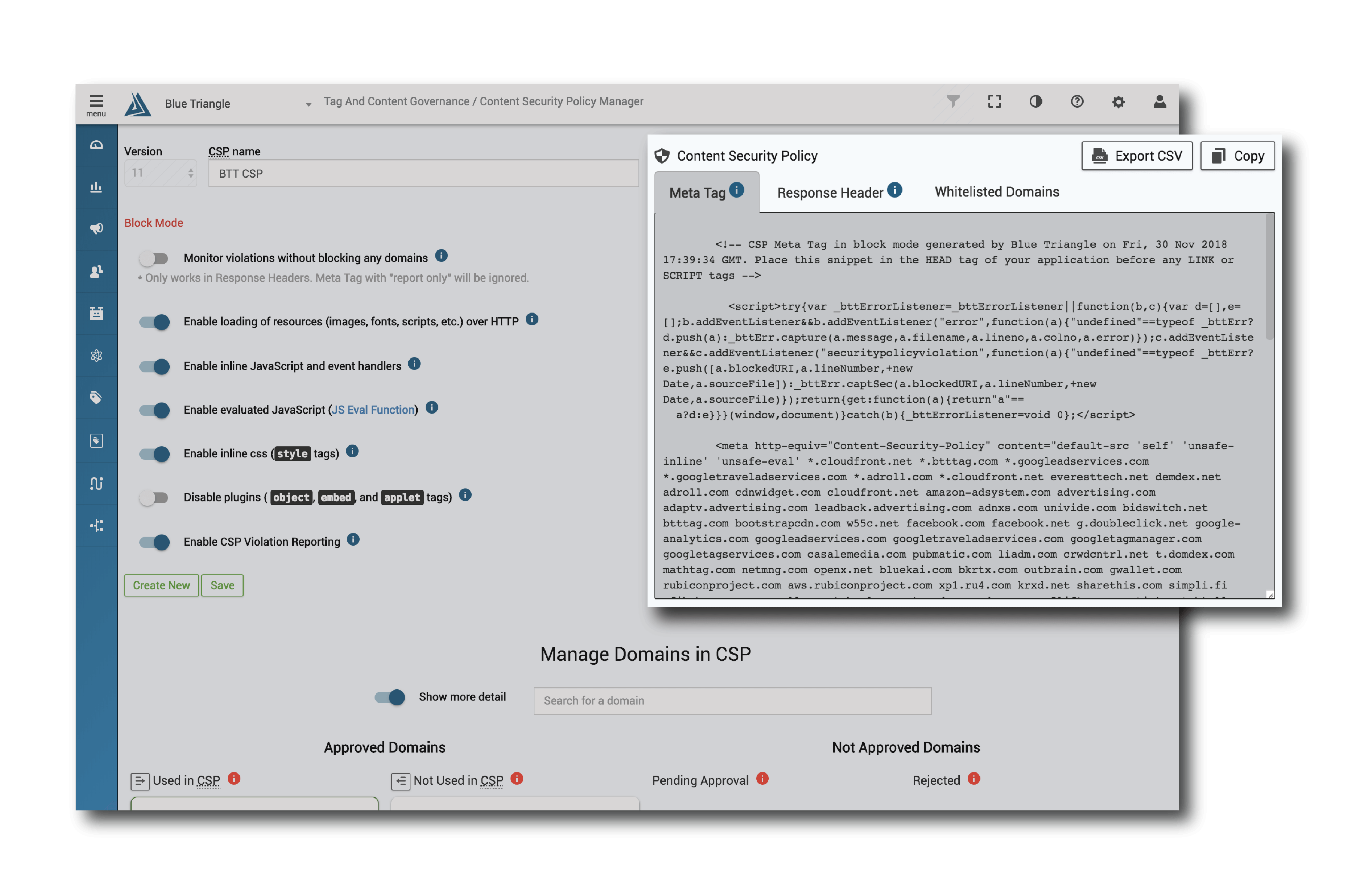
That process is easier said than done, which is why only 7% of the top 500 eCommerce websites in the US have a CSP header in place. We created a Content Security Policy Manager to address this problem - automating the creation and management of your CSP so you can protect your site from Magecart.
Here's the end result inside Blue Triangle:
If you're worried about Magecart...
Protect your site in 24 hours or less by leveraging Blue Triangle to build and manage your Content Security Policy (CSP). Our CSP methodology has protected leading brands from Magecart and other related threats. Let us show you how we can help.
Ready to see our CSP Manager live? Schedule a demo below.
During the holiday rush, every shopper matters
Optimize the customer journey before the eCommerce event of the year.